I remember my early days as a national railway operator CISO, where I literally didn’t know how to prioritize and create a clear roadmap. There I was, scratching my head thinking what should be my next steps. As I wondered how to create my railway organization’s cybersecurity work plan, some of the questions that went through my head were: is the company investing enough in cybersecurity? Are the measures already taken meeting the requirements of the rail industry? Should I purchase additional security systems? which are our most vulnerable railway assets? Is the signaling system really disconnected from the external world, how much money will it cost? how long will it take us to implement a proper solution and more, much more…
Luckily, I had the Israeli National Cyber Directorate by my side, and their doctrine was very well defined – they just released to the public the “CYBER DEFENSE METHODOLOGY FOR AN ORGANIZATION ver 1.0”. This document stated very clearly that:
“You first need to draft a multi-year work plan for the protection of the organization.” and that “As for the construction of the work plan, the organization will define first what it is required to protect, the required protection level, and the protection gaps in view of the desired situation and will, eventually, construct a work plan to reduce the gaps.”
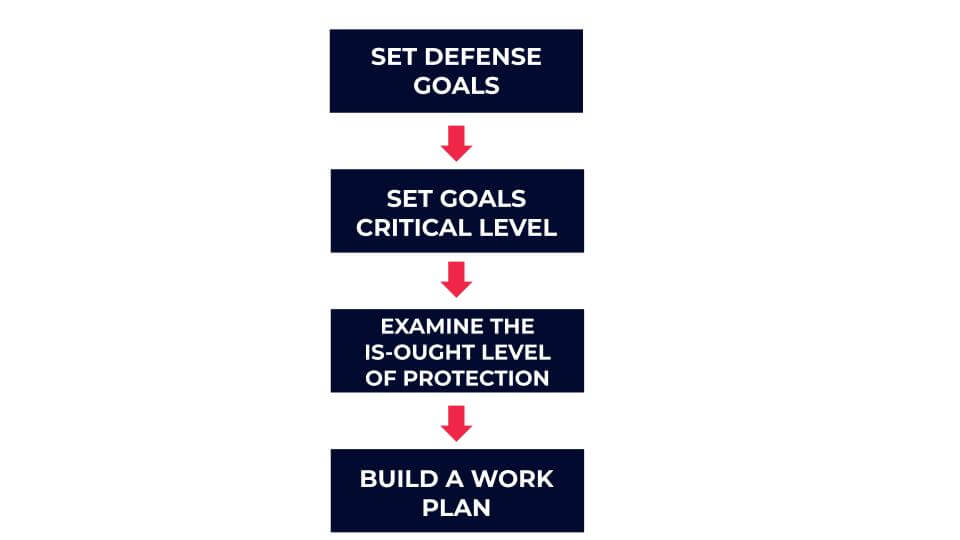
This approach made a lot of sense to me, and it still does. The logic behind such an approach is to look at your organization as a whole, and recognize what needs to be done and when in order to protect the company’s functional continuity and business objectives. Needless to say that risks should be assessed periodically, and this is the baseline for any multi-year cybersecurity work plan.
To achieve prioritization between what needs to be done and when we should determine the weight of the risk level and the cost incurred for implementation (the speed of the implementation of the solution is demonstrated by the size of the circle. The bigger the circle is the longer it will take):
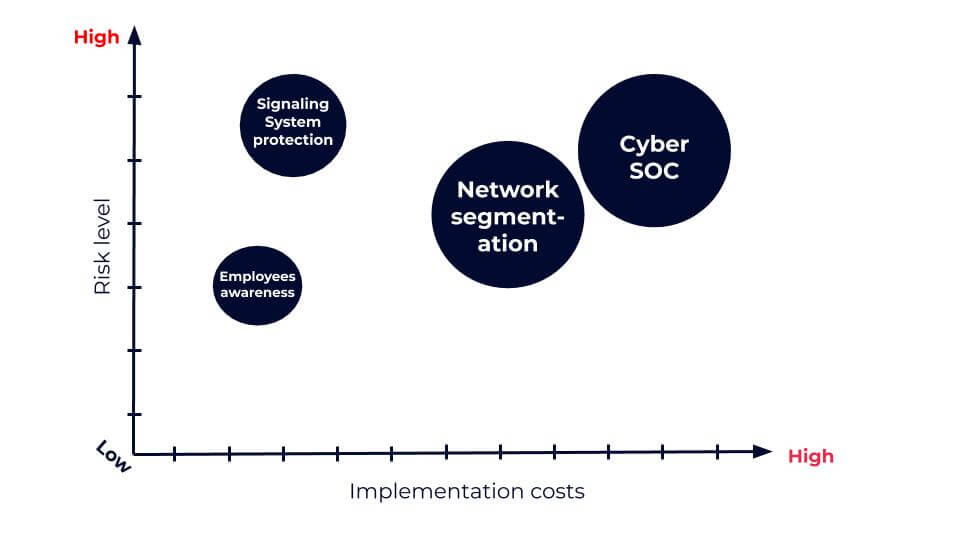
Now, I know it might sound obvious, but it’s always shocking to me to realize how many CISOs begin to implement cybersecurity tools and solutions without first reviewing the policies that are already in place. In my professional view, it’s crucial to first understand where you stand, your high-level business goals, and only then create such a cybersecurity work plan.
The set of available tools that CISOs and CIOs have today are more than enough. Using internal or outsourced services such as Penetration Testing, Security Architecture, and Design, Threat Assessment and Management, and even CISO Consulting – are only a few examples of such methods that can assist the already busy CISO or CIO to recognize the relevant risks, design, and implement a defense response programs, and create a coherent plan to reduce these risks accordingly.

Being part of Cervello makes me prouder every day. The main reason is that as a mission – we invest all of our homeland security and rail cybersecurity capabilities to create a safer, more trusted public transportation service for our children and the future.
Please, do feel free to approach me with any questions about railway cybersecurity, Cervello’s railway cybersecurity platform, our services, or just to discuss cybersecurity in general, as this topic is very close to my heart.

